Introduction: The Importance of EDI
The benefits to businesses of B2B Integration in general and e-invoicing in particular have been widely
documented in multiple reports. An EC report quotes 238 billion Euros, 400,000 tons of paper, 2,700 tons of ink,
160 million litres of petrol as an estimate of what European businesses would save by adopting e-invoice. The
benefits are much larger if one includes other traditional B2B document flows such as purchase orders and
dispatch notes.
The Two Traditional B2B Integration Methods
The two traditional methods of automating data exchanges between business partners (B2B Integration), are either (1) to acquire B2B translation software, or (2) to join a B2B integration environment. The first method is also the most historically common method.
Companies buy (or custom build) and install a B2B communication system within a company’s internal IT environment and organize point-to-point communication with other companies via private networks (X400 network or, so-called value-added networks).
This way of doing B2B integration enables a great deal of flexibility. Participants control the individual B2B relationships and their technical components. However, this method requires a significant investment in money, time and skills. Larger companies have traditionally opted for this method.
Together with the Internet, a second method of carrying out B2B Integration emerged: the B2B integration environment. Point-to-point communication is replaced by a central environment or “platform” which means that one communication to the central environment is sufficient to reach all other partners.
The B2B integration environment enables one to communicate rapidly with a community of trading partners. The value proposition of the B2B integration environment is to create a single technical link between an individual company and the environment. B2B data flows will then be technically organized by the environment. This method corresponds to outsourcing to a third party. It leads to a loss of control and sometimes a loss of speed when the time comes to connect to a new business partner. Medium-sized companies have usually chosen this method.
What’s different about Babelway?
Babelway B2B integration Software-as-a-Service has bridged the 2 traditional methods. Babelway enables customers to connect directly to their partners, avoiding the need for B2B intermediaries. Customers therefore have complete control over their data flows. In addition, Babelway does not require the acquisition of in-house software and infrastructure. Customers can avoid the investment and the operational costs of running a B2B infrastructure and benefit from automated data exchange at much lower costs. The community of Babelway users can share common components of data flows (e.g. the invoice format of Carrefour Belgium) through a catalogue of components which leads to a decrease in the time it takes to build new channel as the community increases.
Babelway offers absolute flexibility to companies of all sizes and at any level of data exchange volumes. They can decide to control data flows or outsource some of it to external IT partners. They can quickly deploy to business partners or stage an on-boarding project based on general business priorities.
This document describes the innovative EDI and e-invoice Software-as-a-Service (SaaS) developed by Tradeshift Belgium. It is addressed to those carrying out an in-depth evaluation of a B2B Integration solution. We also advise these people to register online now to freely discover for themselves what Babelway can do and how it works.
Executive Summary
Babelway B2B Integration Software-as-a-Service (SaaS) allows organizations to automate cross-company processes and enables the secure exchange of structured and recurrent documents such as orders, invoices, pay slips, reports, payment advice, etc.
Tradeshift Belgium has developed Babelway into a widely renowned and respected product in its core field of B2B integration. Babelway processes tens of million documents a year for several hundreds of customers worldwide from very diverse industries like retail, automotive, logistics or fintech.
All it takes to be ready to automate data exchange with ANY business partner or computer application is to register online at www.babelway.net. Babelway guarantees foolproof security, unlimited scalability and first-class performance. Babelway is the solution for rapidly connecting to a trading community while still retaining full control over data flows.
Babelway offers a wide range of functionality to build and administer channels between 2 systems. Babelway supports many communications protocols including Rest API’s, AS2 and AS4, FTP(s), sFTP, email, SOAP, PEPPOL, RosettaNet. Babelway supports many formats, XML, UBL, Excel, Edifact, X12, VDA, CSV and any custom flat-file formats and more.
Babelway is equipped with multiple functionalities such as drag&drop mapping interfaces, message validation, electronic signature, look-up tables, test environment, routing, email notifications, catalogue of ready-to-use components, message tracking, issue management, access and privilege management, capacity and performance management and storage and archiving management.
Babelway software and infrastructure is managed using the strictest quality and security management processes. Babelway information security management system (ISMS) is built according to ISO27001 standard to ensure total security in highly technical environments. Babelway hosting is based on a multi-location strategy with at least 2 redundant data centers for each component of the infrastructure. All systems are permanently monitored by internal and external systems. Storage is encrypted to guarantee confidentiality. Babelway conforms to legal requirements in e-invoicing. Since 2013 Deloitte, KrikPatrickPrice and now KPMG provide ISO27001 certification, SOC1 and SOC 2 reports on the system controls intended to meet the criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Babelway offers helpdesk support. Customers can call upon Babelway professional services to support them with on-boarding partners, designing new channels, developing internal or external communication plans and generally execute projects in relation to the exploitation of the Babelway platform. Babelway also develops partnerships with software vendors and IT integrators to enable customers to find help from the most effective source whenever required.
Babelway regularly organises training sessions and plans to develop a certification program for qualified individuals.
CHAPTER 1: FUNCTIONALITIES OVERVIEW
Babelway Platform is a multi-tenant integration software as-a-service (SaaS). It enables to quickly and cost-effectively automate B2B flows such as EDI messages and electronic invoices across all customers, suppliers, and partners. Leveraging the SaaS model, Babelway helps to streamline the deployment, maintenance, and monitoring of B2B exchanges giving greater confidence and control over business processes. Because Babelway is a cloud-powered integration platform, it offers quick and cost-effective integration to SaaS and on-premise applications. This means that clients can achieve significantly improved data management, more efficient processes, lower enterprise costs, and better resource allocation.
Babelway services are fully available on-demand via a web-browser. There is no software or hardware to buy and maintain in-house, but yet Babelway is still under the full control of its users.
This chapter briefly describes the main functionalities of the software.
Building channels
A channel is the collection of components that must be assembled within Babelway in order to organize an automatic data flow from an external system A to another external system B. The key components are:
- The way in which Babelway is interfaced with system A, called the “gateway IN”,
- The way in which system A formats data, called the “message IN”
- The format in which system B wants to receive data, called the “message OUT”
- The way in which Babelway is interfaced with system B, called the “gateway OUT”
- In between the message in, and message out, we provide an innovative drag and drop transformation step to map from one format to another.
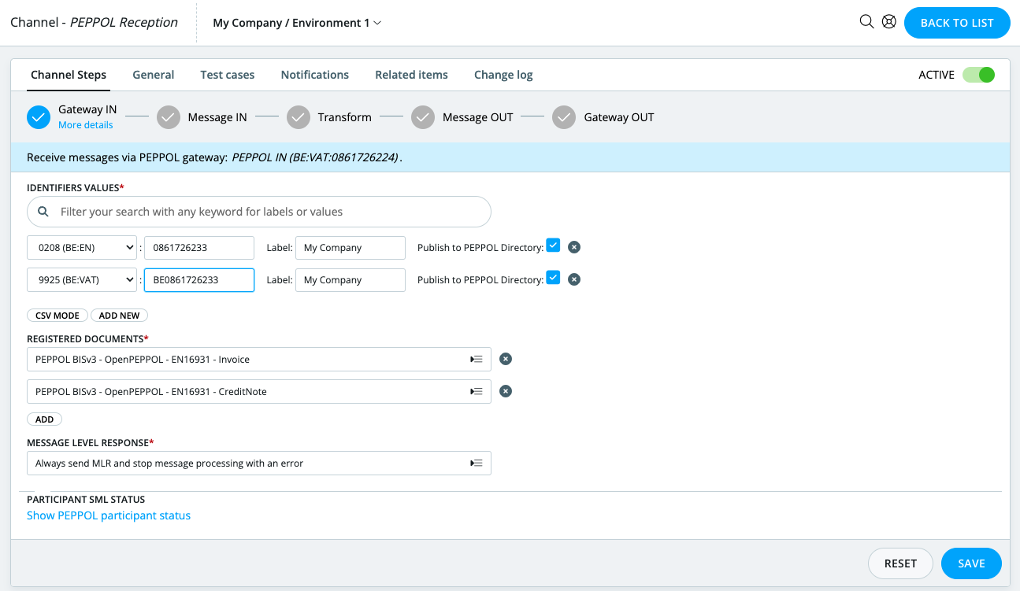
In building channels, Babelway contains the following functionalities:
Configuring communication gateways
Users select how Babelway will communicate with external systems A and B. The communication protocol used with system A can of course be different from the communication protocol used with system B. Users can choose from a range of communication protocols, including:
- Rest API: orchestrated client targeting an public Rest API, like Salesforce, Google Works, Xero or custom systems
- Peppol: the emerging standard for B2B and B2G exchanges in Europe and other places.
- AS2: this a communication standard largely used in retail to secure communication over the Internet.
- Ftp client: to set-up an FTP client accessing an external FTP server.
- Ftp server: to configure the FTP server receiving incoming messages or to place outgoing messages
- Email: to set-up a new Email address to receive incoming messages or to send outgoing messages
- Web gateway: to set-up a website access to upload incoming messages or to download outgoing messages.
- SOAP gateway: to set-up a SOAP gateway (SOAP client) to send outgoing messages to a SOAP server.
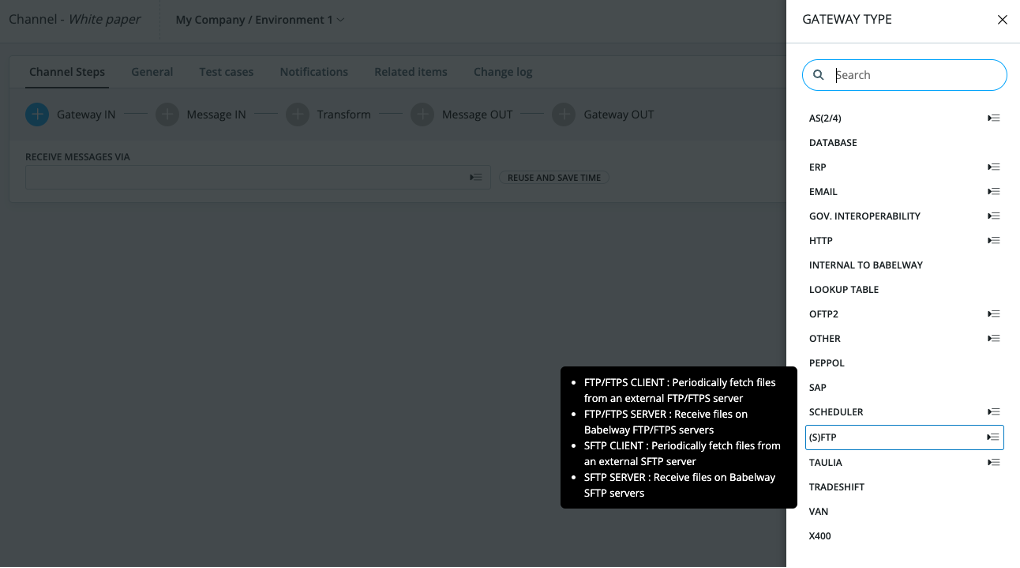
Once the communication technology has been selected, users then fill in the template with the technical parameters that will be used to establish the connection between Babelway and the external system.
If certificates are an element of the communication protocol (e.g. AS2 or FTPs), users will incorporate the external system certificate as a technical parameter. Users will provide the corresponding Babelway certificate to the external system. (See the relevant chapter for details of security and certificate management.)
Note: each Babelway user has its own set of gateway addresses or locators. External systems are therefore connected to individual Babelway users, not to Babelway in general.
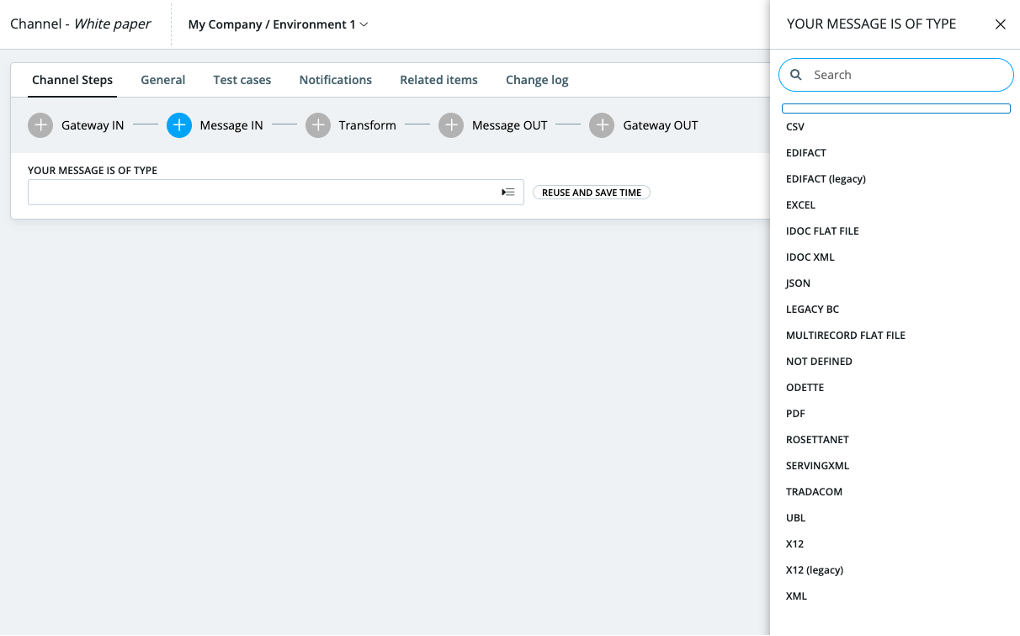
Defining a message definition
Users select the format amongst the following options
- CSV: to define a character-delimited flat file with constant record definition (data is in columns)
- EDIFACT: to define a new message in EDIFACT format
- X12: to define a new message in X12 format.
- MS Excel: to define a new message in MS Excel.
- XML, based on XSD or samples.
- UBL, Universal business language.
- Flat files, delimited of fixed length.
- IDoc xml or flat files.
- And many more…
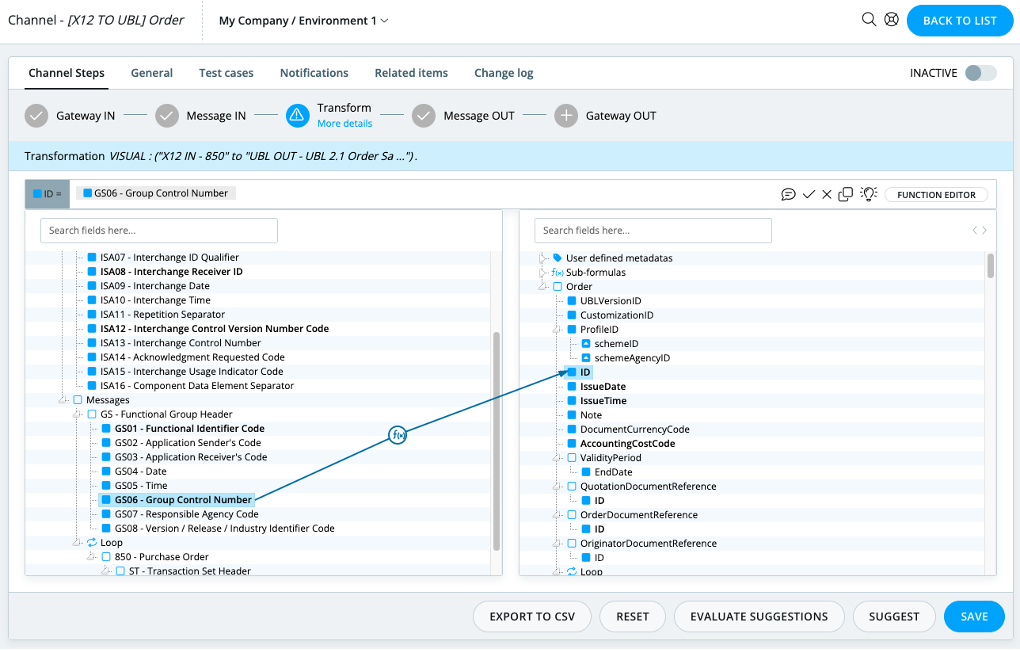
Users can create the transformation rules using the drag & drop interface tool. Users can create correspondences between the message IN and the message OUT by dragging and dropping message fields from left to right.
For more complex transformation operations, users have a portfolio of standard operations they can call upon (concatenation, date formatting, etc.). More advanced users can also define new standard operations using the xpath syntax or xslt functions.
Parsing PDFs
Babelway offers a unique advanced capability to extract information from machine generated PDF documents. This feature prevents costly manual processing by enabling EDI-like processing of semi-structured data.
Creating validation rules
Users can define validation rules to be applied on incoming and/or outgoing messages. For example, validation can make the presence of values in some fields mandatory or make them correspond to a pre-set of values. Validation is particularly useful to prevent that an external system received messages that it cannot process automatically.
Signing outgoing messages
Users can configure channels such that outgoing messages are signed using a dedicated advanced certificate and if the outgoing format enables such signature (must be PDF or ZIP format). (See the relevant chapter for details of security and certificate management).
Creating lookup tables
Users can define and load tables of values, called look-up tables, which are used during the transformation process to change an incoming value into a corresponding outgoing value. An illustrative application of look-up tables is to enable a buyer and a supplier to use different product codes to identify similar products (e.g. GTIN codes versus internal codification).
Building test cases
Users can build test cases of their channels. The test cases enable users to check the result of their work on message formats and transformation prior to deploying a channel into the production environment.
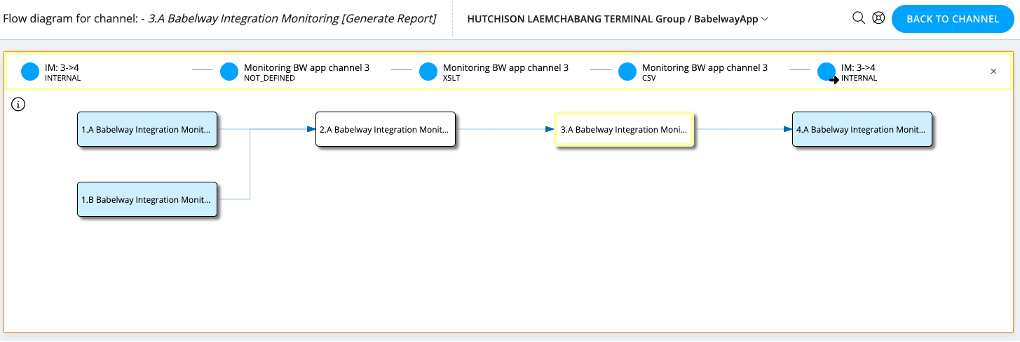
Managing routing across channels
Messages originating from a common source but going to various external systems must be routed. Users can define routing rules based on message content items or on message context.
An visualization tools allows to view the overall interactions between channels:
Managing notifications
For each individual channel, users can build automatic notifications that will send an email to a specified address upon the arrival of a new message. Notified users can be different if the message is successfully processed or an error is generated. Notification can also be sent to another channel for further processing.
Avoiding rework thanks to the catalogue and connectors
Gateway parameters, message formats, transformation and validation rules are created during the channel building process. Each of these items can be re-used in the building of a subsequent channel. This is organized via what we call the catalogue, the place where all new items are listed.
Users populate a new channel from the items available in their catalogue. This catalogue enriches itself progressively each time new channels are built. When users decide to source an item from the catalogue, they make a choice to use the same instance or to duplicate it. This choice is important when making changes to channels. If channels share the same instance of an item, a change in one channel will impact all other channels using the same item.
Activating and deploying components/channels
Users decide which channels and/or components are under construction and which must be activated upon deployment in the production environment of Babelway.
Note: Babelway will soon enable users to open up their catalogue to other selected Babelway users, so that channel items created by one user can be re-used by another user. Functionalities will include the secure management of access rights, the possibility of charging for the use of catalogue items and the possibility of tracking and measuring the usage of catalogue items.
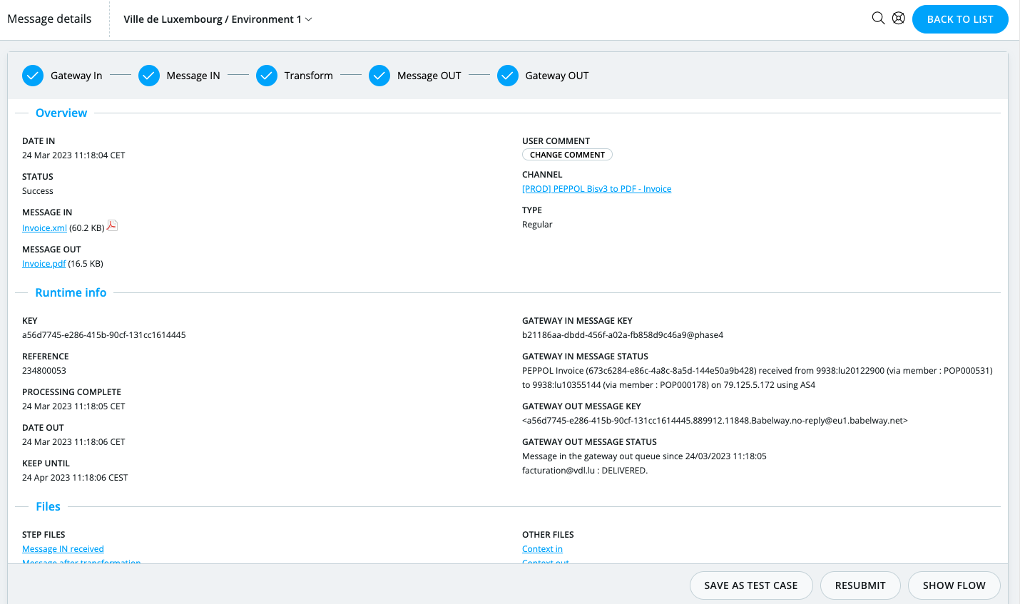
Tracking messages
Messages that flow through the user environment can be tracked and traced. Users have access to any message stored, in all its forms (before, during and after transformation) together with contextual information such as time of entry, time of exist, status, as well as relevant security-related information such as certificates and signatures.
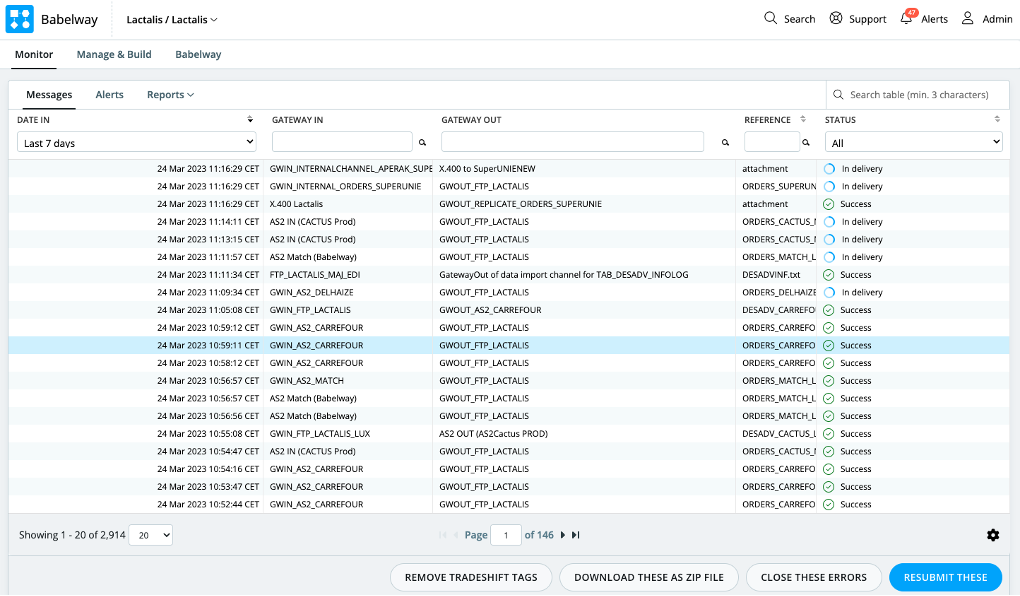
Problem resolution
Messages that are in error can be accessed directly for manual correction and resubmitted in a channel. In this case, a new message is created and the message status of the original message is changed to ‘Error Closed’.
A function to massively resubmit messages is also available to the user.
Long term archiving
The messages stays accessible online to user during the whole retention period, as configured in the environment settings or overwritten in the channel configuration.
During this period, the entire information about the message are kept, including the inbound and outbound messages, all intermediate formats as well as the metadata and processing traces.
Managing Alerts
Multiple events generate alerts. For example, an alert is created when a FTP polling to a remote server cannot be completed due to a connection timeout.
Alerts provide detailed information to users, as well as tools for resolution management.
Account management
The account management function includes the following services:
User management
The administrator of an account can provide other users with access to one of its environments. Access rights are as follows:
- Account ADMIN: All right at the Account level. This data is dependent.
- Environment FULL_ACCESS : All right at the Environment level. This data is dependent.
- Environment HUB_DEFINITION: Generally speaking, allow to view and update existing information at the
Environment level. Cannot manage users. This data is dependent. - Environment OPERATIONS: Can manage users, view and operate exploitation data (messages, tickets, lookup tables) and modify the partners.
- Environment MONITORING: Can only view and operate exploitation data (messages, tickets, lookup tables).
- Environment READ-ONLY MONITORING : Can only view exploitation data (messages, tickets, lookup tables).
- Environment PORTAL USER: Can only view monitoring and partners’ data for a specific list of partners. Can manage other portal users for specified partners.
Environments Management
An account can be made up of any number of different environments. It can be useful to build channels in separate environments if
- different people should have access rights; or
- message storage duration should be differentiated; or
- performance expectations are different
- security requirements demand it
- there is a need for a test environment
Performance management
From very small numbers to 50 millions of messages per month, Babelway is ensuring the timely processing capacity, without being dependent on the general consumption of capacity in other Babelway environments.
Storage management
As a default option, Babelway stores messages for a period of 3 months. Users can select the ‘long-term archiving’ option which provides storage for any period of time up to 12 years.
Other terms of storage (shorter or longer) may be accommodated individually.
CHAPTER 2: TECHNICAL OVERVIEW
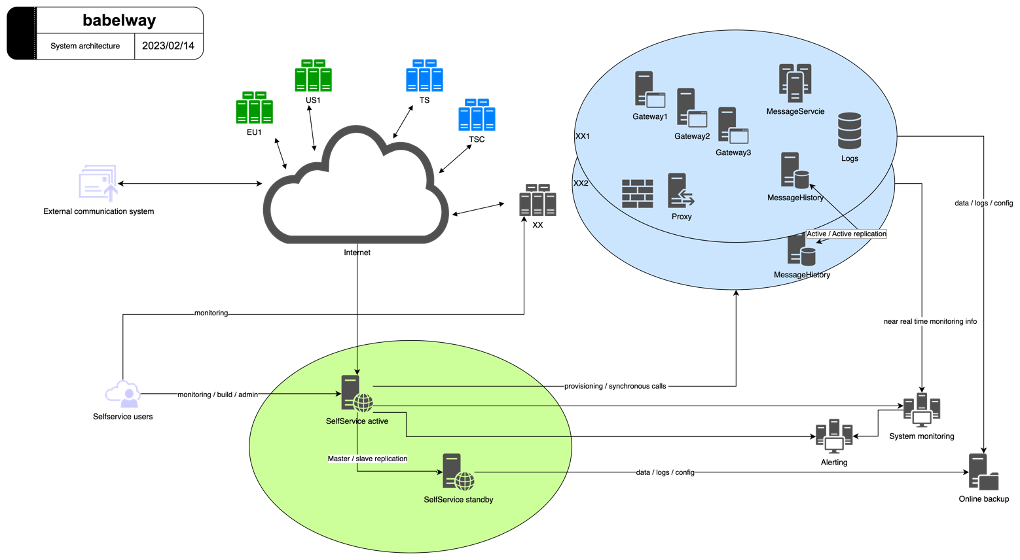
System Architecture
The system, based on service-oriented architecture, enables horizontal scalability and data segregation. The system is mainly divided into 2 parts:
- The SelfService application, a single instance,
- The messaging engine components, multiple instances to support geography and privacy.
SelfService
The SelfService app is the central application of Babelway and represents the “Front-end part” or the “admin console” of the system. It is the only component which is not critical for the messages.
It has the following responsibilities:
- Building channels and components
- Deploying newly created or updated environment components to other runtime systems
- Management of environment
- Creation of users and roles o Environment settings
- Billing
- Monitoring of messages passing via the application
The role of the SelfService is human interaction. There are globally two kinds of interaction with the SelfService:
- Allowing users to define channels and more generally to build configurations
- Showing to users what happened in the messaging engine components. The most important, being which messages have been processed
Messaging Engine
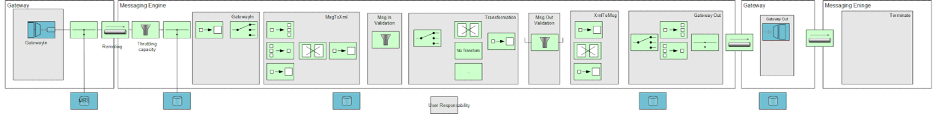
The messaging engine is the set of components responsible for the processing and storing of messages. The messaging engine transforms the incoming message (format defined by the message definition in) into an internal xml representation of the message and applies the business validation and transformation defined by the user in the selfservice. The resulting XML file is then transformed to the final format (defined by the message definition out).
Please see a simplified diagram of the processing:
System Management
Infrastructure Management
Babelway has a multi-vendor approach to infrastructure. It has agreements with two hosting providers:
- Amazon Web Service (AWS) servers are physically located in Europe, the US, and China.
- Combell, a recognized Belgian hosting company. Servers use the physical premises located in Belgium.
Our hosting providers have demonstrated to Babelway that they manage infrastructure according to our (SOC2, SOC1, ISO 27001 and GDPR) expectations levels.
To maximize availability and reliability, not only has Babelway contracted on strict terms with reliable partners, but it has also installed redundancy between at least 2 data centers. In the event of downtime of one of the 2 data centers, Babelway can switch all data traffic to the other data center.
Limitations of the redundancy are:
- Web interfaces (human access to user environments) has an active node, with a real-time passive backup. In case of unavailability of the Active infrastructure, messaging services can continue but human tracking
or maintenance is not available, until the Passive node is activated. - Gateways to external systems based on physical IP addressing would also be interrupted. We recommend that users use URL locators instead of IP addressing wherever possible.
Private Cloud
The processing and archiving of messages are achieved by a separate component called the ‘messaging engine’. The messaging engine is self-sufficient to process messages, even if temporarily disconnected from the web interface.
This approach technically allows customers of Babelway to host their messaging themselves while still using the unique Software-as-a-Service. This could be important to some customers if security considerations require them to control the messaging servers themselves or to have servers physically located in some specific geographic territory, for example.
Default Geographic Location
Babelway customers hosted on the shared infrastructure have the possibility to choose the geographic location of their messaging engine between an EU location, a US location, or a CN location.
Software Management
Babelway software development uses, on the backend, Java as a programming language and XSLT for data manipulation. It uses JavaScript for the web front-end. The infrastructure runs on Linux and uses PostgreSQL as the main database engine.
These components have been integrated into an extensive development program which began in October 2006. Our technical developments are centrally managed in Belgium. We have developed a very precise expertise on highly specific topics such as scalability, database optimization, ergonomy, cryptography, processing performance, data standards.
Software development follows the SCRUM framework for software and other platform development. Our sprint horizon is 2 weeks.
CHAPTER 3: QUALITY AND SECURITY MANAGEMENT
Audits and Quality Management
SOC1 AND SOC2 TYPE 2
Babelway issues a SOC2 Type 2 report since 2013 and a SOC1 Type 2 report since 2022. They are yearly audited by KPMG for Security, Availability, Processing Integrity, Confidentiality, and Privacy. This conformity is equivalent to the past SAS70 norm, which certifies the quality of the Security Procedures.
ISO 27001 CERTIFICATION
Babelway is ISO27001 certified since 2017. Babelway’s policy regarding security can be consulted online at: https://www.babelway.com/security-policy.php . The system ensures processes are in place to meet the policy’s objectives.
SOC1, SOC2 full reports and ISO27001 certificates are available upon request at: support@babelway.com
Data Security
To ensure the total data independence between environments, Babelway software strictly controls data access using isolation techniques.
The system is based on RBAC (role-based access control) principles. Each software layer (presentation, application, business and data) performs its own security enforcement.
An external penetration testing is organized every year. Human effort, bug bounty program and several internal tools are constantly looking for software and system vulnerabilities.
Data in Transit Policy
All internal communications between components or with external services like S3 containing customer data are encrypted with industry standard technology, currently TLSv1.2.
The setup of the security for the communication with external parties is under the responsibility of the user. By nature of the integration service the platform is providing, Babelway accepts support for the longest reasonable period older algorithms. The safeguards for this are:
- a close monitoring of the traffic to decommission weak and unused algorithms as soon as possible
- a clear decommissioning plan published to end users to decommission inacceptable protocols.
Data at Rest Policy
Several layers of encryption are used to protect data at rest:
- Server full disk encryption: all disks containing customer data are fully encrypted using an industry
standard technology, currently AES-256. - Hashed information in database: if possible, sensitive information is stored hashed in the database.
- Encrypted information in database: if not possible, sensitive information is stored encrypted in the database and decrypted on usage, using a password stored outside of the database itself. For instance for gateway credentials
- Archived data policy: Information stored for archiving, like backups, must be encrypted with industry standard technology, for instance GPG with a recent algorithm. Passwords and keys are rotated every year.
Audit Trail and Traceability
All accesses to environment and customer data are logged in an audit trail. The audit trail is using a separate business logic to insure independence of the regular business logic. It cannot be modified by Babelway support agents. The audit trail is proactively inspected on a weekly basis for critical operation and odd usage patterns.
Monitoring
Monitoring of systems and applications are performed using different mechanisms:
- An external monitoring tool is used to test the availability and the performance of the application from a customer point of view. This system also includes a 24/7 alerting mechanism to the mobile device of the operator in charge. An escalation process is also in place to ensure proper handling of issues.
- An internal monitoring tool is used to test the availability and performance of the different components of the system. The Operations Manual provided in annex describes the set of monitored items
- A positive & reactive monitoring to alert the Operation Manager when a situation requires some attention (for instance, a message entering the system and is not delivered in the SLA window)
All tools are collecting information, generating statistics and delivering alerts if needed. Issues and bugs encountered are logged and tracked for further reference and follow up.
CHAPTER 4: USER SUPPORT
Help Desk
The human monitoring function provides helpdesk support to users on working days. Any request or issue reported is acknowledged within 15 minutes. It is given a support alert number and a reply is provided within 1 hour at the latest.
The support agents are distributed among 3 different levels, each one having his own expertise field. Below is a non-exhaustive list of examples of issues, distributed according to the level structure:
Level 1: This is where all support tickets begin. This level is able to provide:
- Assistance and help on system
- Messages follow-up (message not sent/received, message is in error)
- Basic troubleshooting like issue in mappings
- …
Level 2: If an issue cannot be resolved in level 1, it will be escalated to level 2. This level is able to solve issue like:
- Protocol incompatibility
- Problem linked to a bug in the application code -…
Training
Babelway has developed an online basic and advanced training program called the Babelway Academy. More specific training sessions can also be provided by Babelway senior staff as required.
Professional Services
Customers can call upon Babelway professional services to support them with on-boarding partners, designing new channels, developing internal or external communication plans and generally execute projects in relation to the exploitation of the Babelway platform.
For each project, Babelway and the customer agree on a scope and a price based on man-day prices referenced in the price list. Account management and general interventions requiring human involvement are defined with each customer within the scope of Babelway professional services.
Network of Partners
Babelway develops and entertains a network of partners with specific capabilities in geographic regions, industrial sectors or technical domains. These partners can also be called upon in some customer projects.